This is the first in a multi-part series analyzing the potential of security tokens in the world of crypto assets.
2017 was the year of crypto. Bitcoin became a household phenomenon and increased ~13x in value, Ethereum spurred interest in decentralized applications (dapps), and ICOs became the newest speculative rage.
By contrast, 2018 is shaping up to be a year of maturation for crypto. The SEC has made it clear that they intend to oversee the industry. While some may dislike regulation, it does bring with it a sort of legitimacy and it should deter bad actors. In 2018, we expect to see the emergence of the security token.
The intent of this series is to explore the security token market and better understand the use cases and opportunities. In part 1, we’ll outline the basics of utility tokens, security tokens, and what makes something a security. Future parts will dive into specific analyses of opportunities.
From the highest level, it’s useful to delineate coins from tokens, which both fall under the higher-order bucket of cryptocurrency. Generally, coins operate on an independent blockchain with their own set of rules. It may be a native blockchain like Bitcoin and Ethereum or a fork of another blockchain like Litecoin (of Bitcoin). Coins are typically useful as mediums of exchange and/or a store of value. By contrast, tokens are typically built on top of an existing platform, like Ethereum, and add their own rules and functionality to an existing platform.
Tokens can be further broken down into two categories: utility tokens and security tokens.
- Utility tokens give holders access to a specific protocol or network, oftentimes enabling them to use an associated product or service. With utility tokens, no ownership rights to the underlying company behind the associated product or service are granted to token holders.
- Security tokens grant holders ownership rights to an underlying asset. In essence, they are asset investments governed by the protocol set forth by the associated blockchain.
Utility tokens are the most common type of token in existence today. Two examples of utility tokens are:
- Filecoin – a decentralized file storage platform. Users can pay participants in the network to store files on participating computers’ unused hard drive space. Filecoin is similar to Google Drive or Dropbox, but with no centralized storage location.
- Golem – a decentralized computing platform. Users can pay participants in the network for unused processing power from participating computers. Golem is a decentralized Amazon cloud compute platform.
The important takeaway is that utility tokens grant the right to participate in a network, not ownership of the network.
What makes something a security? The SEC determines whether something is a security under the Securities Act of 1933. The Supreme Court case of SEC v. W. J. Howey Co is often referenced here, which resulted in a structured test whether or not an offering qualifies as an “investment” and requires registration.
An important clarification needs to be made about the use of the word “security.” As an industry, the crypto world has adopted the term security token to represent ownership in an underlying asset as described above, but the SEC uses the word security to define a broad set of investment instruments, which they regulate. This could mean that utility tokens are also recognized as securities according to the Howey Test.
The Howey Test. If a token (or another instrument) meets all of the following criteria, the SEC considers it an “investment.”
- The user is investing money.
- The user expects to profit from the investment.
- The investment is in a “common enterprise.”
- Any profit comes from the efforts of a third-party or promoter.
The first part of the test is fairly easy and most tokens pass. Users are always investing money. This part of the test has been expanded to include the investment of other “assets” in subsequent court cases. Some cases have defined money as “any form of consideration with value.”
The second part, whether or not users expect a profit, is often the case in token raises today. Many of the networks and protocols that are offering utility tokens through ICOs aren’t live at the time of the ICO, so the argument that a holder simply wants access to a particular network (and doesn’t expect to profit) is a difficult one. If there were no expectation of a profit on the side of the ICO utility token buyer, it would make more sense to wait until the project is live before purchasing tokens. Where there is risk, there is reward. We’ve seen some tokens ask for “donations” in order to see a project launched. These tokens offer “consideration of allocation” when a project is live. This seems like a semantic workaround that the SEC probably won’t accept, but companies are likely to continue to try.
The third part of the test talks about whether or not the investment is in a “common enterprise.” Different courts have had different definitions of common enterprises. Some federal courts refer to a horizontal commonality and count the pooling of assets for investment in a common enterprise. Other federal courts refer to the vertical commonality and count the efforts of a third-party or promoter. With two broad definitions, it seems likely that most tokens will be considered a common enterprise.
The fourth part addresses whether or not the profit comes from the efforts of a third-party or promoter. This test is often passed by tokens, as there are always individuals working on the project or network. The profit would derive from their efforts in building a better network.
Applying the Howey test, it’s clear that security tokens will be “investments” and require registration with or exemption from the SEC. This likely isn’t a major issue because security token issuers and investors will likely anticipate regulation in this manner. However, if the SEC applies the Howey test to utility token offerings, it may ultimately determine many of those offerings are also securities and regulate them as such.
Regulation and issuance of security tokens. Issuers of security tokens will have several different filing options with the SEC:
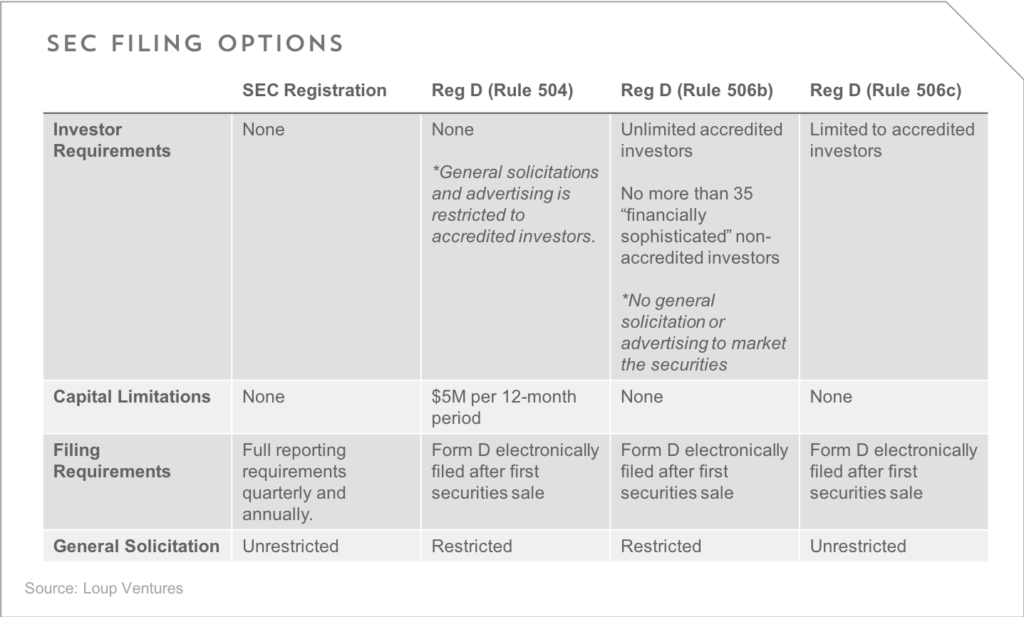
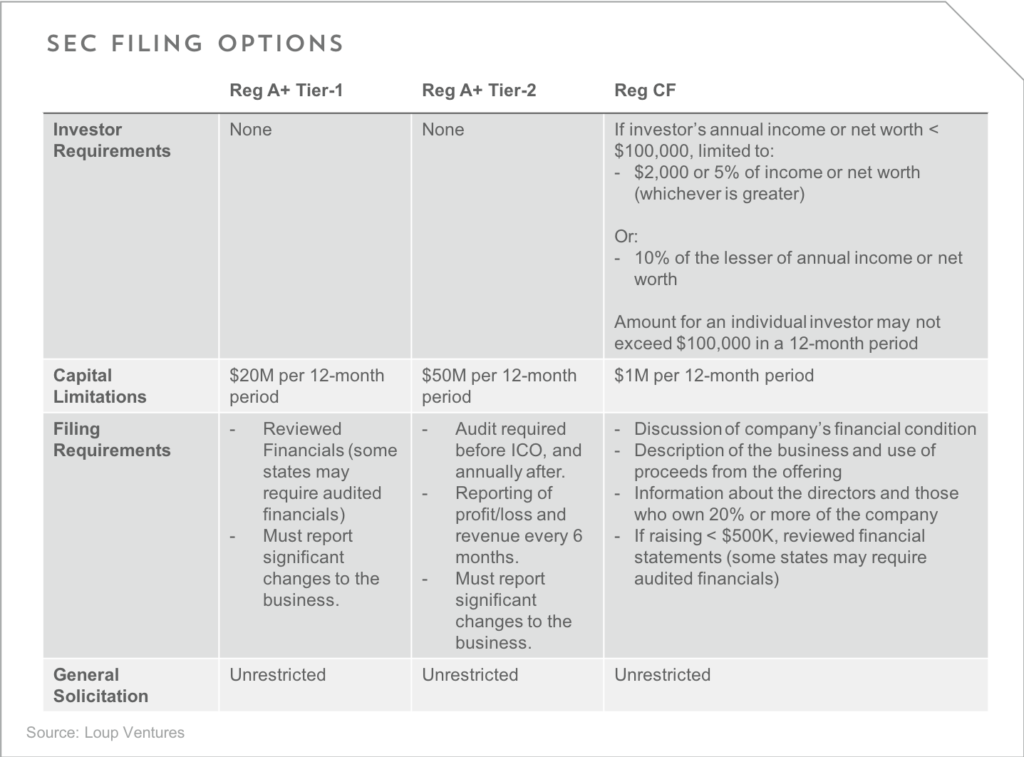
While the SEC hasn’t issued much specific direction regarding security token offerings (STOs) or ICOs, we expect many companies issuing security tokens to follow Reg D (Rule 506c) or Reg A+. Some high profile ICOs have moved to only offer tokens to accredited investors, like Telegram, allowing them to file under 506c. We expect this to be a continued trend given current market demand among large investors.
Security tokens face three major problems today. Despite there being relatively more regulatory clarity on security tokens versus utility tokens, there are some challenges that security tokens face before they become a more widespread investment option.
- Security tokens have limited liquidity options for investors. Today, investors in security tokens don’t have the same liquidity options as other crypto assets, which is arguably the biggest issue for the asset class. There are effectively no exchanges that exist to trade security tokens. To offer trading of assets that the SEC classifies as “investments,” exchanges must meet strict know-your-customer (KYC) standards and Anti-Money Laundering (AML) requirements. While there are some exchanges (e.g., Coinbase) that attempt to meet these standards, they are often the ones that offer the fewest cryptocurrencies and tokens to trade. Depending on the security token, exchanges may need to be set up to interact with dividends, distributions, or communications with customers about things like proxy voting. Because of the additional regulations imposed on exchanges listing “investments,” many existing exchanges have avoided security tokens. There are a few exchanges under development for security tokens (see tZERO), but it will be some time before these exchanges are launched and have sufficient trading volume.
- Current securities laws aren’t easily adapted and pose additional complications. The Howey Test is a good place to start for security token regulation, but there may be additional regulations required for token-based securities. For example, many in the crypto community want transactions to be anonymous or pseudo-anonymous, which makes compliance with KYC and AML standards difficult. The SEC may need to offer additional guidance on what is and is not acceptable when it comes to anonymity and security token ownership. Exchanges that offer trading of security tokens may also require additional regulation.
- There are unique technical challenges in creating security tokens. Security token creation faces different challenges than utility token creation. The stakes are not only higher, but additional securities requirements come into play. Beyond the security and compliance issues, security tokens may also need to include instructions on how to handle dividend payments, coupon payments, splits, voting, and other common functions of securities. Finally, security tokens need to be flexible enough to allow for changes in the terms of the security, which may be difficult after issuance.
A few companies like Polymath and Harbor see these technical challenges as opportunities and have set out to simplify these issues and make it easy for companies to issue security tokens.
What’s next? We’re going to dive into what a security token exchange might look like, and how it would compare to existing securities exchanges.
Disclaimer: We actively write about the themes in which we invest: virtual reality, augmented reality, artificial intelligence, and robotics. From time to time, we will write about companies that are in our portfolio. Content on this site including opinions on specific themes in technology, market estimates, and estimates and commentary regarding publicly traded or private companies is not intended for use in making investment decisions. We hold no obligation to update any of our projections. We express no warranties about any estimates or opinions we make.